What Vulnerability Assessments Reveal About Your Network Security
Key Takeaways
- Vulnerability assessments are crucial for identifying and addressing security weaknesses in your network.
- Regular assessments help prevent potential cyber threats and data breaches.
- Comprehensive assessments can improve overall network performance and security posture.
- Implementing vulnerability assessments requires a strategic and proactive approach.
Introduction to Vulnerability Assessments
Vulnerability assessments are a fundamental component of a robust network security strategy. These assessments involve identifying, quantifying, and prioritizing vulnerabilities in a system. By systematically examining various network elements, organizations can gain critical insights into potential security gaps and take appropriate corrective actions to mitigate those risks. Knowing how vulnerability assessments uncover critical network weaknesses is essential for any organization looking to enhance its cybersecurity defenses and safeguard sensitive data from unauthorized access and potential breaches.
Understanding the Assessment Process
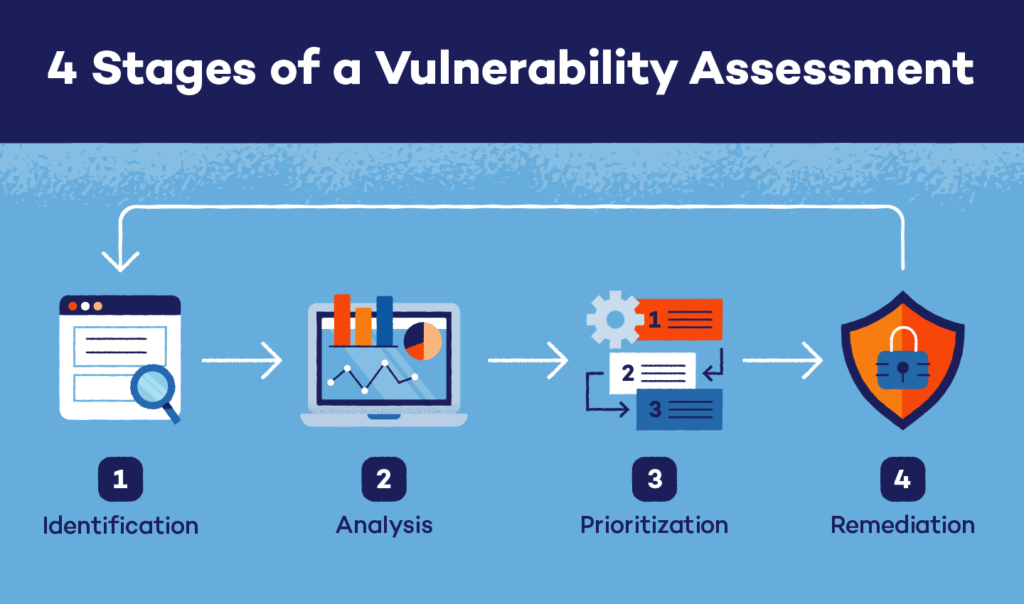
The vulnerability assessment process typically entails several steps: identifying assets, scanning for vulnerabilities, analyzing results, and implementing remediation measures. Initial steps involve cataloging all hardware, software, and network assets to create a comprehensive inventory. This is followed by using advanced scanning tools to detect vulnerabilities within these assets. After uncovering potential weaknesses, a detailed analysis determines each vulnerability’s severity and potential impact. Finally, remedial measures are prioritized and implemented to mitigate the identified risks.
Common Vulnerabilities Revealed
Common vulnerabilities discovered during assessments include outdated software, misconfigurations, and weak passwords. Each of these vulnerabilities can pose a significant risk if not addressed promptly. By conducting regular assessments, organizations can stay ahead of potential threats and maintain a strong security posture.
Outdated Software
Running outdated software can expose your network to known vulnerabilities that may have publicly available exploits. Regular updates and patches are crucial for safeguarding against such exploits by addressing software flaws and enhancing system defenses.
Misconfigurations
Misconfigurations in network devices, servers, and applications are common issues that can create security loopholes, providing entry points for attackers. Ensuring proper configuration settings and adhering to security hardening guides are vital for minimizing risk and preventing unauthorized access.
Weak Passwords
Hackers employing automated tools can easily crack passwords that lack complexity or are commonly used. Implementing strong password policies and encouraging the use of multi-factor authentication can significantly enhance security by ensuring credentials are not easily compromised.
The Role of Automated Tools
Automated tools play a crucial role in vulnerability assessments. These tools can rapidly scan large networks and provide detailed reports on potential vulnerabilities, saving time and resources compared to manual assessments. Some popular options include Nessus, OpenVAS, and Qualys, each offering unique features and capabilities. Automated tools also provide continuous monitoring, enabling organizations to detect and respond to new threats in real time.
Benefits of Regular Assessments
Regular vulnerability assessments offer numerous benefits, including enhanced security, compliance with industry regulations, and improved network performance. Identifying and addressing vulnerabilities regularly can prevent potential breaches and ensure the continuous protection of sensitive data.
Enhanced Security
Organizations can stay fortified against evolving threats by regularly identifying and mitigating vulnerabilities. Proactive assessment allows for timely interventions, reducing the likelihood of successful attacks and minimizing the impact of any security incidents.
Compliance with Regulations
Many industry regulations and standards, such as GDPR, HIPAA, and PCI DSS, mandate regular vulnerability assessments to protect sensitive data. Staying compliant helps avoid legal and financial penalties and reinforces an organization’s commitment to maintaining high-security standards and gaining customer trust.
Improved Network Performance
Addressing vulnerabilities can improve network performance by optimizing configurations and applying the latest updates. Properly secured and maintained networks experience fewer disruptions, increasing productivity and reduced downtime.
Challenges in Conducting Assessments
Despite the many advantages, conducting vulnerability assessments comes with its own set of challenges. Resource constraints, such as limited budgets and personnel, can make it difficult to conduct comprehensive assessments. The complexity of modern networks, with their numerous interconnected devices and systems, adds another layer of difficulty. Additionally, constantly evolving cyber threats require continuous effort and vigilance. However, leveraging automated tools and following best practices can help mitigate these challenges and ensure thorough and effective assessments.
Implementing Best Practices
To maximize the effectiveness of vulnerability assessments, organizations should implement best practices such as conducting assessments regularly, prioritizing vulnerabilities based on risk, and involving stakeholders from various departments. Additionally, continuous monitoring and updating of security measures are essential to stay ahead of threats.
Regular Assessments
Conducting assessments at regular intervals ensures that new vulnerabilities are identified and addressed promptly. This proactive approach minimizes the window of opportunity for attackers and keeps the network defenses robust. Regular assessments also help track the progress of remediation efforts and identify recurring issues that need attention.
Prioritizing Vulnerabilities
Not all vulnerabilities carry the same level of risk. Prioritizing vulnerabilities based on their potential impact allows organizations to allocate resources efficiently and address the most critical issues first. Factors such as a vulnerability’s exploitability, severity, and potential impact should be considered when prioritizing remediation efforts.
Stakeholder Involvement
Involving stakeholders from different departments, such as IT, management, and compliance, can provide a comprehensive view of the organization’s security posture. Collaborative efforts in addressing vulnerabilities ensure that all network aspects are covered and appropriate measures are taken to protect sensitive data and maintain operational continuity.
Conclusion
Vulnerability assessments are vital to network security. By regularly identifying and addressing vulnerabilities, organizations can protect their networks from threats and improve their security. Implementing best practices and utilizing automated tools can help ensure that assessments are thorough and effective. Proactively conducting these assessments will lead to a more secure, resilient, and efficient network environment.




